In our recent webinar with Veeam, we reviewed why you need a security plan for Microsoft 365. When Microsoft 365 was officially announced in 2017, it came as the next obvious evolution of the already powerful collection of Microsoft office tools. From a collaboration perspective, it provides an elegant solution to connect and empower remote team members. From an IT perspective, it streamlines IT management of users, devices, apps and services. And best yet, it uses integrated, intelligent security to safeguard company data, customer data, and intellectual property. If security is already baked into the software, why do you need a security plan for Microsoft 365?
Webinar recording: Microsoft 365 Security and Backup: Why You Need It.
Organizations Need Multiple Layers of Security
You’ve probably heard this before: organizations need multiple layers of security. Like a castle protected with moat, walls, guards, and royal decrees about what thou canst and canst not do, your business has equivalent layers of security protecting its employees and assets. Each castle has different kinds of protection depending on what it’s resources and possible attackers are and these layers of protection add up to create the total defenses.

Your particular “castle” may or may not include alligators, depending on your specific needs.
Using a layered approach to security is key in the information technology world as well. Each business has different needs, and that what’s good for one organization isn’t always going to be good for another. Microsoft 365 represents just one piece of an organization’s larger security plan, and the default security setting may or may not be in alignment with that business’ needs. Luckily, your MSP can help you identify what you need to do to build your own customized quality cyber security plan.
Core Aspects of a Quality Cybersecurity Plan
What are the core aspects of a quality cyber security plan? There are six key areas your IT team focus on to keep your organization safe:
- Perimeter security
- Endpoint protection
- Information security
- Authentication protocols
- Backup and disaster recovery
- Network monitoring
The first two key areas of a quality cybersecurity plan are perimeter security and endpoint protection. An example of perimeter security would be a firewall that provides physical network endpoint protection. The firewall protects endpoints connected to the network, or the endpoints include antivirus or content filtering as part of their connection profiles.
Information security is the third area of a quality cybersecurity plan. It provides role-based access control around data security. The fourth area concerns authentication protocols, which includes Two-Factor Authentication (2FA) or Multi-Factor Authentication (MFA) and identity access managers or providers. The fifth area is backup and disaster recovery, one of the most critical pieces of any cybersecurity plan. Best practices restore files from backups in cases of a disaster or breach.
The last key area of a quality security plan is to identify and track activity within a network with network monitoring. This includes monitoring the following areas:
- Who’s connecting to the network
- What devices are connecting to the network
- Where the connections come from
- Network activity
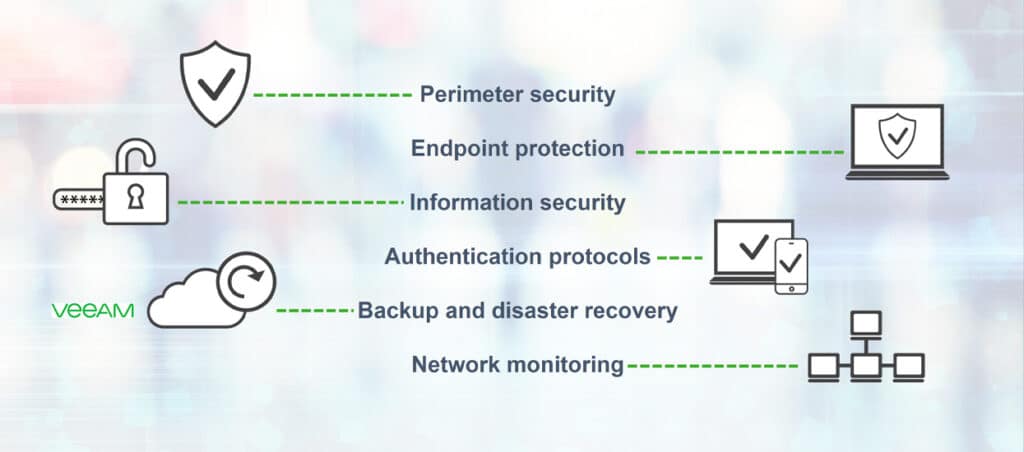
The six critical aspects of a quality cyber security plan: Perimeter security, endpoint protection, information security, authentication protocols, backup and disaster recovery, network monitoring.
Infrastructure Changes = Threat Changes
The six key focus areas of a cybersecurity plan are the same no matter what kind of infrastructure your business has. Originally, IT equipment and networks were located primarily on premise and protected by a firewall. Bad actors could compromise one system to gain full network access.
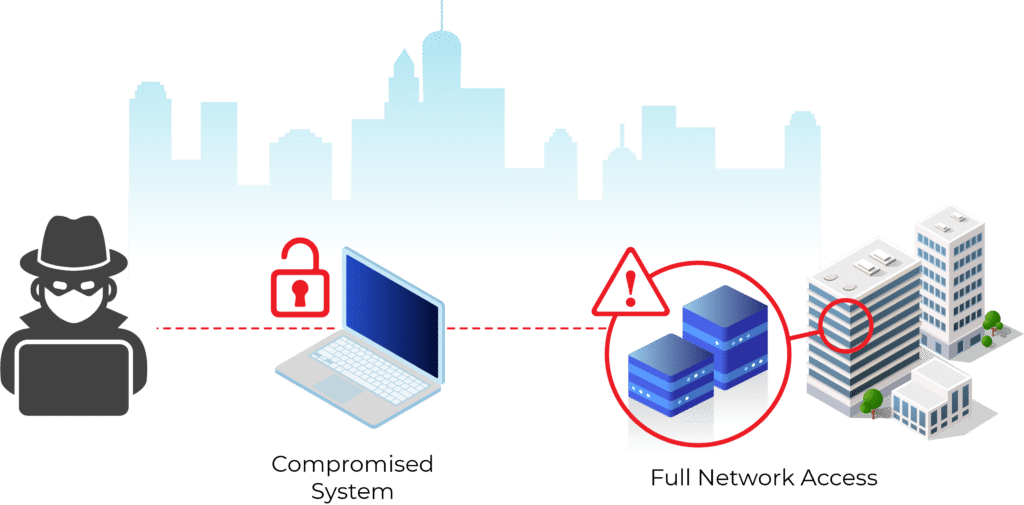
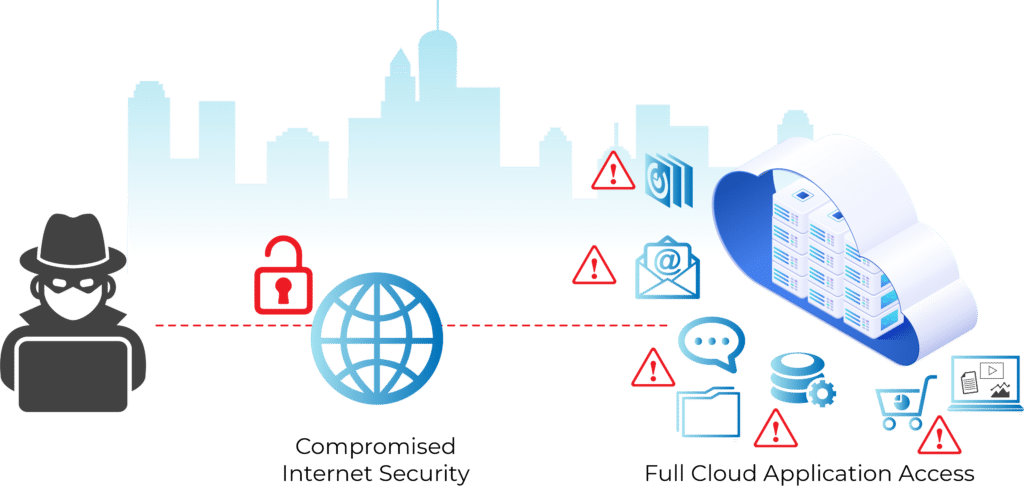
Today, organizations use either on-premise, cloud, or hybrid systems. Hackers gain access to SAAS and cloud-based applications and data in a similar way that they did to on-premise networks: by finding a weak security link. This time, instead of compromising a system to gain access to a network, a hacker uses weaknesses in an organization’s internet security to gain full cloud application access. Microsoft 365 is just one of many of these SAAS applications that can be used as an entry point.
Before You Plan, Understand Your IT Security Posture
Organizations combat different types of cyber threats by providing the correct training, tools, and policies to support their particular infrastructure. The reason no two security plans are the same is because no two organizations are the same.
Picture the training, tools, and regulations surrounding a regular commuter car vs. a 18 wheeler. Each vehicle rides on the same roads, yet each is very different when it comes to maintenance and handling requirements. Would you develop a maintenance plan before you understood which vehicle you owned and what it required?

In a similar way, it is critical to understand your current IT infrastructure and current security posture before you come up with a security plan for your organization.
Ask these questions to summarize your basic IT security posture:
- What applications are you using?
- What should you be monitoring?
- Which devices are in your environment?
- Who has access to your environment?
You or your MSP can use CIS-18 as a guide to help you identify and prioritize areas where you are most vulnerable. Recently updated by the Center of Internet Security from CIS-20 to CIS-18, this new list consolidates the CIS Controls by activities rather than by the team member who manages the devices. Most importantly, for cloud users and companies using SAAS like Microsoft 365, it gives guidance on how enterprises can safely manage their cloud services.
What are the Microsoft Security & Compliance Centers?
When you understand your current IT security posture you can build your IT security plan. This plan helps improve your current posture to the security level where your organization wants to operate.
The Microsoft Security and Compliance centers are portals specifically designed to manage, track and investigate the various security and compliance features of your Microsoft 365 environment.
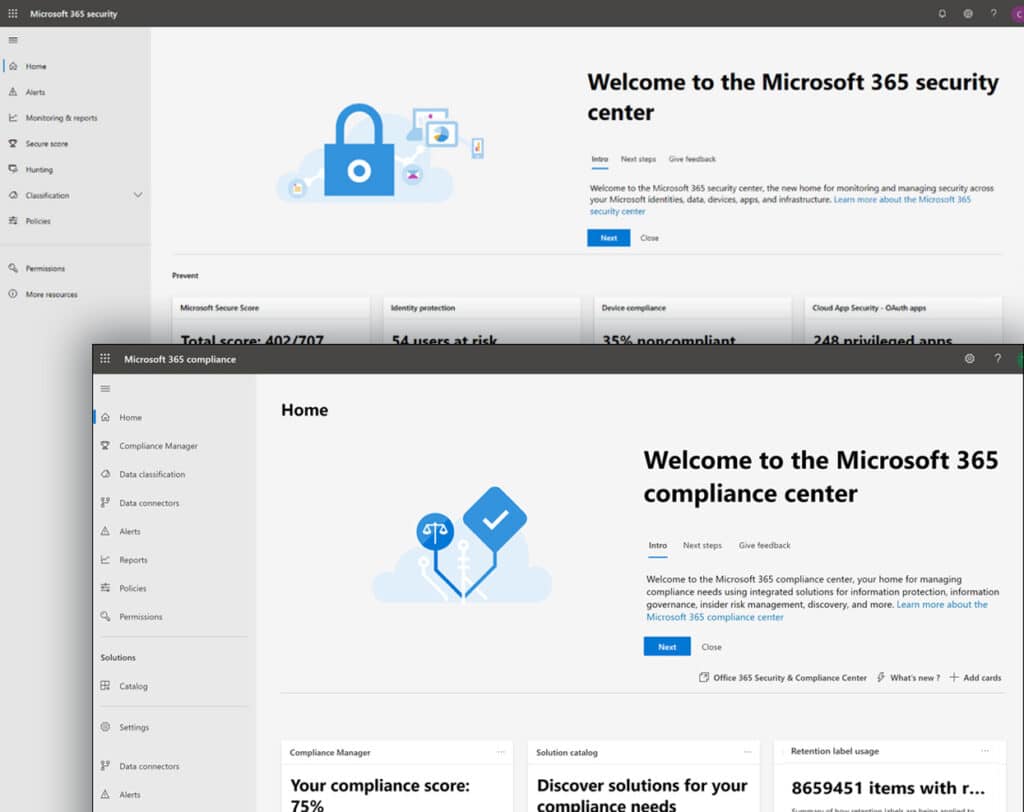
The default security and backup settings within M365 might be sufficient for your business needs, or they might not. You can adjust your settings based on your needs or utilize an outside company to provide services beyond what Microsoft has to offer. For instance, Veeam provides extensive backup and disaster recovery services ideal for businesses who have stringent backup requirements. Your MSP can help you do a risk analysis to determine if you fall into this category. Always make sure that the security features you use, whether they are integrated into M365 or come from an outside service, support your business continuity IT strategy.
The Microsoft Security and Compliance center portals will show you a security score for various areas. Your ideal score is determined by what the acceptable risk for your business is in that area. If you’ve decided to accept a higher risk in a particular area, ensure that you have a mitigation plan in place to overcome this risk should an incident occur.
Additionally, the secure score also shows you the impact score of the different policies and improvement actions. These reveal details that are inherent to your configuration with M365, the devices, and the users.
Six Steps for Getting Started with your New M365 Security Plan
The Microsoft Security Analytics team identifies the latest risks and threats and notifies users. They know that communicating specific attack vectors of those threats to users is extremely important for organizational policy changes. Here are the six steps you need to ensure your M365 security environment is integrated into your organization’s broader security plan.
- Microsoft Compliance Score. Review your Microsoft Compliance Score to improve your compliance score.
- Configure Risk Management Policies. Configure insider risk management policies to help minimize internal risks and easily detect threatening activities in your organization.
- Data Loss Prevention Policies. Review your organization’s data loss prevention policies and make changes if necessary.
- Microsoft Cloud App Security. Set up Microsoft Cloud App Security and get familiar with it.
- Communication Compliance Policies. Communication compliance policies help identify and correct corporate policy violations as soon as possible.
- Review Alerts & Risks. Make sure you review alerts or potential risks.
In Summary
Why do you need a security plan for Microsoft 365? Your business is not automatically protected by the Microsoft 365 built-in security features. You need to understand how to use the features to execute your organization’s security plan.
Like the fortifications of a castle, IT security requires a layered approach. First, assess your IT security posture. Next, make a requirements list based on your business needs. Finally, dedicate resources to monitor key areas and periodically review and update policies.
The Microsoft Security and Compliance centers help you track your security and compliance posture so you can make adjustments to your security activities. Sometimes, your organization requires additional services outside of what Microsoft 365 has to offer. If necessary, have your MSP coordinate with an appropriate security service provider to meet your security and compliance goals.
