We recently teamed up with PBO Advisory Group and Franklin | Soto to present the top best cyber practices to help protect your organization’s valuable IT and financial assets. The 5 top IT security habits we shared in the webinar will help your business get started right away with a better IT security posture.
Listen to the full webinar, “Hacking Is on the Rise.”
Hacking Is on the Rise
Small- to medium-sized businesses are targets of cyber attacks and need to be intentional about finances, security, legal conformity and insurance. The COVID-19 environment has unfortunately leveled the playing field for a lot of cyber criminals. Criminals take advantage of small- to medium-sized businesses who are unprepared for the technical considerations of the work-from-home environment.
Cybercriminals uncover and exploit increasing numbers of vulnerabilities every day. Big companies are paying out huge ransoms, including Colonial Pipeline and JBS. The Scripps attack resulted in a shutdown of three weeks, a number devastating to any business, let alone in a hospital trying to take care of patients and inpatient/outpatient care.
What we don’t hear about in the news is the attacks to small- and medium-sized businesses. The price they pay is smaller and not as headline-worthy, but in reality close to 60% of all cyber attacks target small businesses. Why are the majority of cyber criminals focusing their attacks on SMBs? Simply, SMBs often do not have best practices in place to prevent or recover from an cyber attack, making them easy targets.
Hackers Target Employees
Our employees are our greatest assets, but they are also our greatest vulnerability. Negligence, whether intentional or unintentional, leaves a company vulnerable to attack. Contractors, employees, or anyone that might have access to corporate information must go through periodic awareness training to keep businesses safe.
The Cost of a Data Breach is High
A data breach costs a company in several ways.
- Hard Costs
- Soft Costs
- Reputation
Hard costs include actual out of pocket costs, such as breach notification mailings, post-breach monitoring, and fines. Soft costs include things like loss of revenue, increased insurance, and tracking software. Reputation damage can hurt or cripple business and relationships with both existing and future customers.
The IT Security Mindset Shift
There has been an instrumental shift in the way that we approach how to protect our information. Even as late as five years ago, systems were designed “not to fail.” In this old mindset, IT security depends on system designs that prevent every single attack into the network.
Fast forward to today. We understand that that mindset is no longer realistic. You can’t protect yourself against every single attack. Cybercriminals generate new attacks every second of every day and look for every way they can to get into your system. Today’s IT security mindset focuses on resiliency and assuming compromise.
Our top 5 IT Security Habits are built around this new mindset of resiliency and assuming compromise. The habits focus on how to best keep data protected and dispersed throughout multiple different media and systems. That way, when an attack occurs, a business can quickly restore, recover, make sure the information is secure, and respond to those attacks as quickly as possible.
5 Top IT Security Habits
Habit #1: Technology Protection
The first habit we recommend is to put some basic technology protections in place, including things like virus, spam, and malicious content protection.
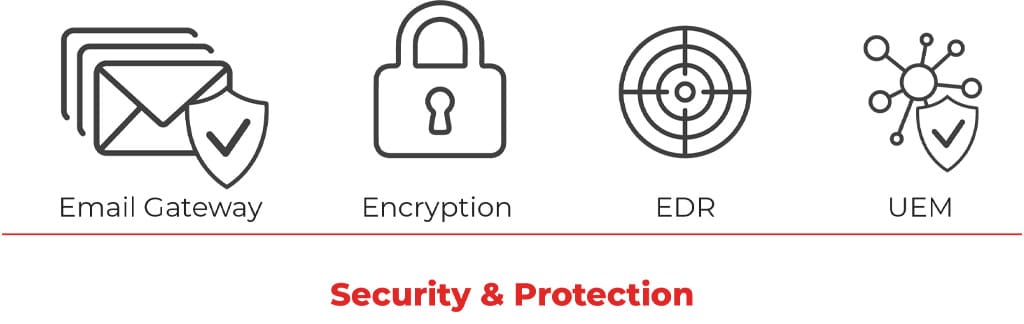
- Email Gateway Services: software that helps filter malicious spam
- Encryption Services: Protects personal identifiable information (PII)
- Endpoint Detection and Response (EDR): EDR quarantines, isolates and remediates a known compromise across your network.
- Unified Endpoint Management and Mobile Device Management: Identify, manage and track any connected devices and software within your environment.
Habit #2: Access Control
There are a number of access control measures small- and medium-sized businesses do to protect themselves.
- Strong Passphrase: Passphrases combine a series of words with symbols and numbers into an easy-to-remember phrase. They are harder than regular passwords for a cybercriminal to crack because they might be 27 characters long, and easier for users to remember.
- Multi-factor Authentication (MFA): MFA reduces risk considerably. A required authentication code is pushed to a separate device each time users sign in to an application or website. This makes hacking nearly impossible.
- Virtual Private Network (VPN): A virtual private network enables users to securely connect to a private network through a public network.
- Mobile Device Management (MDM): MDM accounts for all devices within a company network, whether they are employee or company property.
- Single Sign-on (SSO): SSO ensures credentials are protected within a centralized location. Users update a single passphrase every 90 days and securely log into multiple systems from a single, controlled access point.
Habit #3: Training Employees
Training is critical to educate our employees on cyber safety. A typical training exercise a company does with their employees are phishing simulations. Here’s a prime example of a real phishing email that we received here at centrexIT. The email looks like an urgent request for a phone number from James Desson, our president.
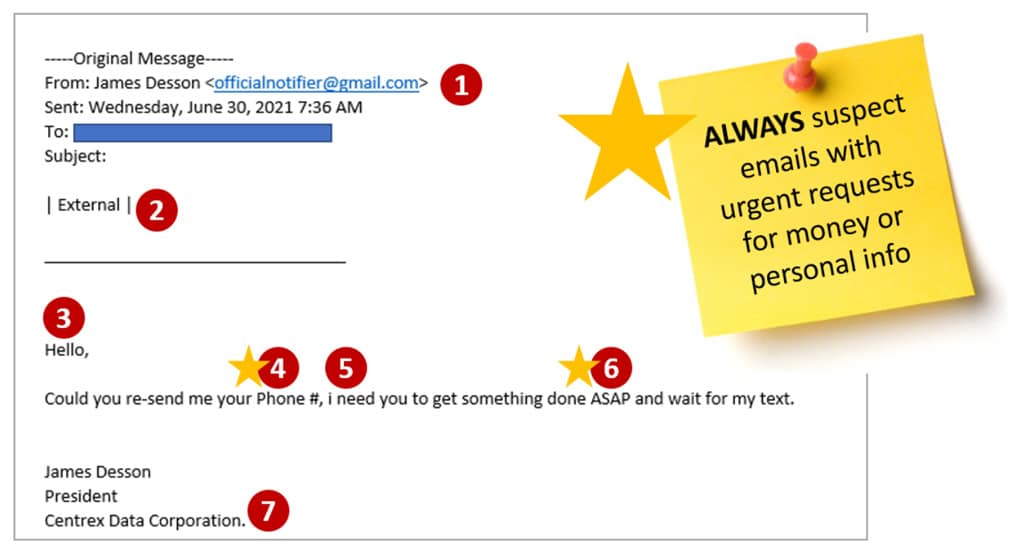
Always be suspicious of any email with urgent requests, especially for money or personal information. Other clues that this is a phishing email include:
- Email address is not coming from correct company url.
- This email is marked as “External.” Emails from the company’s president should come from an internal source, not an external source.
- Generic greeting does not use the person’s name.
- Request for personally identifiable information (PII).
- Poor grammar.
- Urgent request.
- Signature has misspelled company name.
Take a look at our Cybersecurity Essentials Packet to learn more about basic training options available for employees.
Habit #4: Policies & Procedures
Policies and procedures are absolutely necessary for the success of your business. At a minimum, every company should have a business continuity plan (BCP) and information security policy as protection for when disaster strikes.
A disaster does not have to be a pandemic or natural disaster. It can be system access or an attack by a cybercriminal. A BCP details responsibilities, actions and a clear set of steps for response and recovery from disasters. Once policies are in place, test the disaster recovery strategy at least once a year. The goal is to know exactly the steps that need to be taken to be up and running as quickly as possible.
Another important policy, especially with the increase in remote work, is a Bring Your Own Device (BYOD) policy. Many employees utilize personal mobile devices for work purposes. Businesses must advise employees on the following:
- The risks associated with having company data on a personal device.
- The level of control required by the business.
- Responsibilities and expectations on what to do with company information.
Habit #5: Backups
Frequent backups are critical. One of the most important actions you can take as an organization is ensure your backups are regular and tested. At a minimum, periodically do a simple test restore. Once a year, do a full system restore as part of your disaster recovery plan. Increase the frequency of your full system restore based on your business needs.
We recommend clients use the 3-2-1 backup rule when developing a backup strategy.
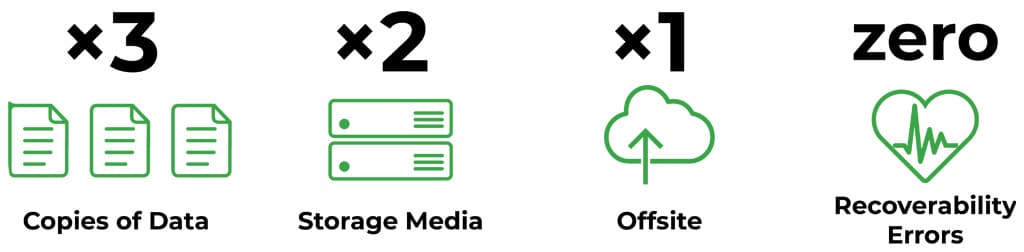
The 3-2-1 backup rule states you should have at least three copies of your data on two different types of storage media for redundancy. At least one of these backups should be at an offsite geographic location.
When you restore those backups to the desired systems, the idea is to have zero recoverability errors. Zero recoverability errors is is not always achievable, but it’s a good goal to regularly test to. The more we test, the more we can reduce errors. Our position is strong to restore and resume business practices when attacks occur.
In Summary
In summary, our top five IT security recommendations are:
- Technology Protection, including virus, spam, malicious content protection
- Access Controls, including strong passphrases, multi-factor authentication, virtual private network, mobile device management, single sign on.
- Training Employees, including email phishing campaigns, stack attack simulations, and security training courses.
- Policies and Procedures, such as a Business Continuity Policy, Incident Response Plan, or Bring Your Own Device Policy
- Backups, including frequent tests and frequent restorations.
Still unsure how to get started? We’re here to help. Contact us today and we’ll walk through an IT security plan that’s built for your business.
