Cybersecurity Defense
Vulnerability Scanning
Risk Assessments
Compliance
Penetration Testing
Policies
Security Strategy
-
 Cybersecurity DefenseHow can you effectively defend against unknown threats? Businesses must know what they are protecting and what points of entry to monitor in order to protect against cyber threats.
Cybersecurity DefenseHow can you effectively defend against unknown threats? Businesses must know what they are protecting and what points of entry to monitor in order to protect against cyber threats.
-
 Vulnerability ScanningVulnerability scans protect your business from cyber threats by continuously assessing your weaknesses from the inside of your network. A rigorous process reduces business risk by using the scans to identify and fix weak points.
Vulnerability ScanningVulnerability scans protect your business from cyber threats by continuously assessing your weaknesses from the inside of your network. A rigorous process reduces business risk by using the scans to identify and fix weak points.
-
 Risk AssessmentsMany industries require businesses — and sometimes their third-party vendors — to complete risk assessments. These assessments provide objective insight against a standard industry framework about where risk can be expected.
Risk AssessmentsMany industries require businesses — and sometimes their third-party vendors — to complete risk assessments. These assessments provide objective insight against a standard industry framework about where risk can be expected.
-
 ComplianceRegulation compliance requires alignment between policies, controls, people, and processes. Many government regulations necessitate compliance for certain types of businesses to operate. Compliance is not a switch that can be turned on overnight — it can take years for companies to reach a high level of compliance.
ComplianceRegulation compliance requires alignment between policies, controls, people, and processes. Many government regulations necessitate compliance for certain types of businesses to operate. Compliance is not a switch that can be turned on overnight — it can take years for companies to reach a high level of compliance.
-
 Penetration TestingDo you know how vulnerable your business is from outside attacks? Penetration tests help organizations test their security, and are sometimes an industry requirement. Security professionals use a variety of tools and methods to attempt to gain access to a company's network to see what can be accessed.
Penetration TestingDo you know how vulnerable your business is from outside attacks? Penetration tests help organizations test their security, and are sometimes an industry requirement. Security professionals use a variety of tools and methods to attempt to gain access to a company's network to see what can be accessed.
-
 PoliciesWhat regulations do you follow? What policies will ensure adherence? A business must make decisions regarding policies and determine what is an appropriate stance to take to protect their systems.
PoliciesWhat regulations do you follow? What policies will ensure adherence? A business must make decisions regarding policies and determine what is an appropriate stance to take to protect their systems.
-
 Security StrategyDeveloping a game plan for how a business is going to protect the critical assets of a company is commonly the responsibility of the executive leadership team. Having a clear security strategy in place decreases risk significantly and increases the likelihood for a business to continue to operate without incident.
Security StrategyDeveloping a game plan for how a business is going to protect the critical assets of a company is commonly the responsibility of the executive leadership team. Having a clear security strategy in place decreases risk significantly and increases the likelihood for a business to continue to operate without incident.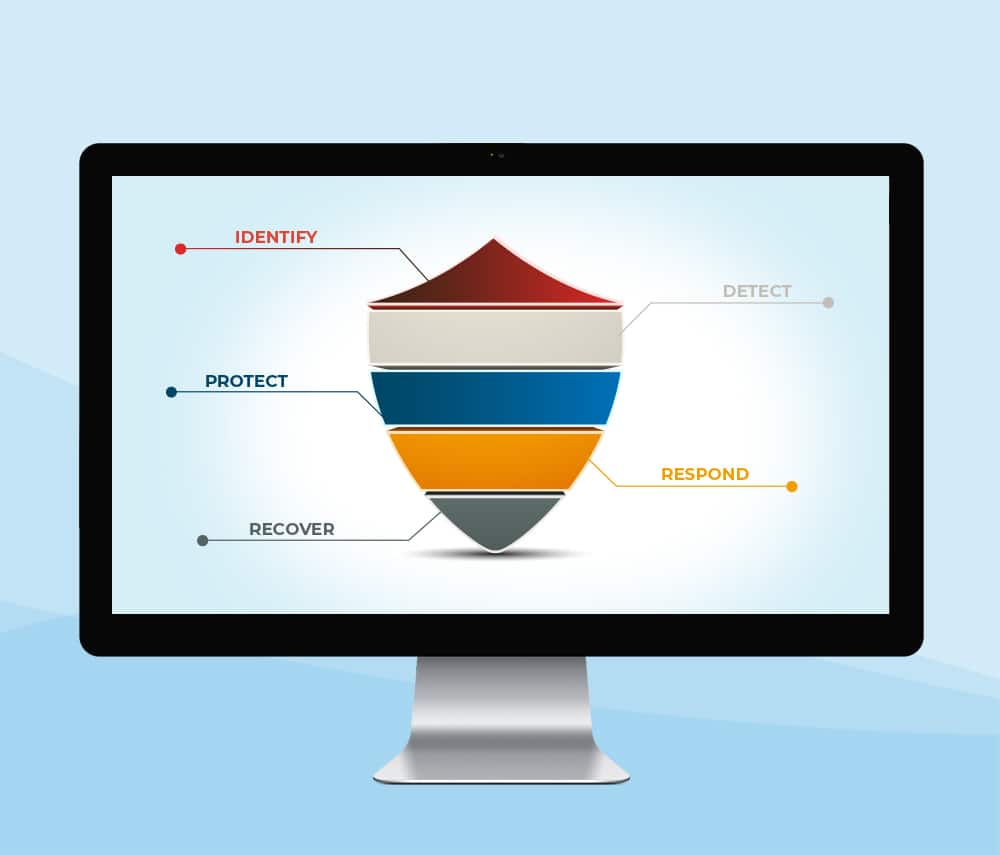
Take Control of The Threat Landscape
Our offerings help you get a proactive cybersecurity and compliance plan
in place that’s built for your business and helps you stay compliant.
Microsoft 365 Security & Security Hardening
We can help you assess, harden and manage the built-in security features of your new Microsoft 365 business solution. Our Microsoft 365 security and security hardening offerings are best suited for SMBs looking to reduce their cybersecurity risks while leveraging modern workforce tools.
Cybersecurity Essentials
Trained and aware employees are critical to securing an organization, and an effective, ongoing internal security awareness program can help reduce your company’s vulnerability. These three cybersecurity essentials offerings — Email Phishing Simulations, Security Awareness Training, and Dark Web Monitoring — all help set your employees up with the skills they need to be your business’s first line of defense against online crime.
Risk Mitigation Platform - Essentials
This offering is an essential set of risk mitigation entitlements for up to 25 IP addresses. Entitlements include:
- Asset Discovery & Management
- Remote Monitoring & Alerting
- Vulnerability Scans
- Policy Creation or Revision
Risk Mitigation Platform - Advanced
This offering is an advanced set of risk mitigation entitlements for up to 100 IP addresses. Entitlements include:
- Asset Discovery & Management
- Remote Monitoring & Alerting
- Network Security
- Endpoint Security
- Vulnerability & Penetration Testing
- Policy Creation or Revision
- Risk Management
- Phishing Campaigns
- Continuous Compliance Management
- File Integrity Monitoring (FIM) Capabilities
- Cloud Security
Risk Assessments
Risk assessments support regulatory requirements and best practice guidelines from several regulatory entities, making the services technically enforceable as a policy so businesses remain compliant. Use of Automated Cyber Risk Management tools and Compliance Assessments help identify potential risks and threats so action can be taken to reduce the chances of a data breach. Offerings follow the requirements defined by the Center of Internet Security (CIS20), General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA).
Overview of Entitlements
A business relies on its assets. Having a monitoring and alerting system and training your employees helps protect your IT environment by keeping you in a proactive position to respond to each potential risk before a vulnerability becomes an issue. Read through our entitlement descriptions to get an idea about which of the above guardIT cybersecurity packages would best suit your business needs.
Asset Discovery & Management
We work with you to validate & track your assets.
Cloud Security
Cloud assets are monitored by installed agents and any security events that arise are analyzed.
Continuous Compliance Management
Identify risks and correlate to the required compliance of two of the following sets of regulatory requirements: HIPAA, PCI DSS, ISO 27001, CCPA, GDPR, and DFARS.
Dark Web Monitoring
Cybercriminals traffic and buy stolen credentials so they can infiltrate your networks to steal your data. By monitoring the Dark Web for threat intelligence about stolen user data associated with your company’s domains, you can be alerted when a compromise is detected, so that you can respond to stop a potentially costly and widespread data breach.
Email Phishing Simulations
With ever-changing threats present, it is important that your employees are exposed to all the latest phishing traps set by criminals. Email phishing simulations test employees on how they would respond to a real-life phishing attack. We’ll track which employees have clicked on a phishing email, who has given away their password and who has ignored the email.
Endpoint Security
We remotely analyze the security of endpoints connected to the network and outside the network. Includes monitoring endpoint devices and analyzing hardware and software configurations.
File Integrity Monitoring (FIM) Capabilities
Our File Integrity Monitoring (FIM) solution detects changes to files and directories effectively in near real time, and trigger events based on specific criteria. These events are monitored 24/7 to ascertain if there is any malicious or suspicious activity.
Managed Security
Our managed security provides 24/7 monitoring with management and review. Our security analysts provide actionable insights to improve your security posture, and they have rapid response identification and reaction to cyber threats.
Network Security
To track security-related issues: we monitor events or changes on your network and wireless devices, analyze hardware and software settings, assess vulnerabilities, and analyze network traffic.
Policy Creation or Revision
We work with you to determine what kinds of policies you need and get them produced.
Remote Monitoring & Alerting
We track and analyze behaviors, patterns and security trends on your network, then alert when needed to keep your network safe.
Risk Management
We give you and your third party vendor a risk assessment to understand the risk posture of all the assets, policies, processes and security controls. Then we analyze the risk identified and apply the security control to reduce the risk.
Security Awareness Training
Our Online platform contains easy-to-understand, short and visually engaging training videos include an Online quiz to verify the employee’s retention of the training content. As the threat landscape changes, our platform is continuously updated with the most up-to-date relevant training content to keep your line of defense alert and strong.
Vulnerability & Penetration Testing
We conduct regular vulnerability scans and penetration tests, and make recommendations based on the analysis of the reports.